Airwatch is a one of the best modern management platforms around. Depending on your environment, you may use Airwatch already, or you might be using Intune, or another management platform. We are using Airwatch currently, despite being heavily into Office 365 (and getting further into Windows 10), so that is what this post is about.
Why connect with REST API? Because you can then do it from the command line, and you can perhaps use something like Powershell to script tasks automatically, or which can't be done in the console.
Configuring Airwatch
I will asssume you have admin rights on the console. You will need to log on, and get the token. This is found in settings, under System>Advanced>API>Rest API. There you will find an API key.
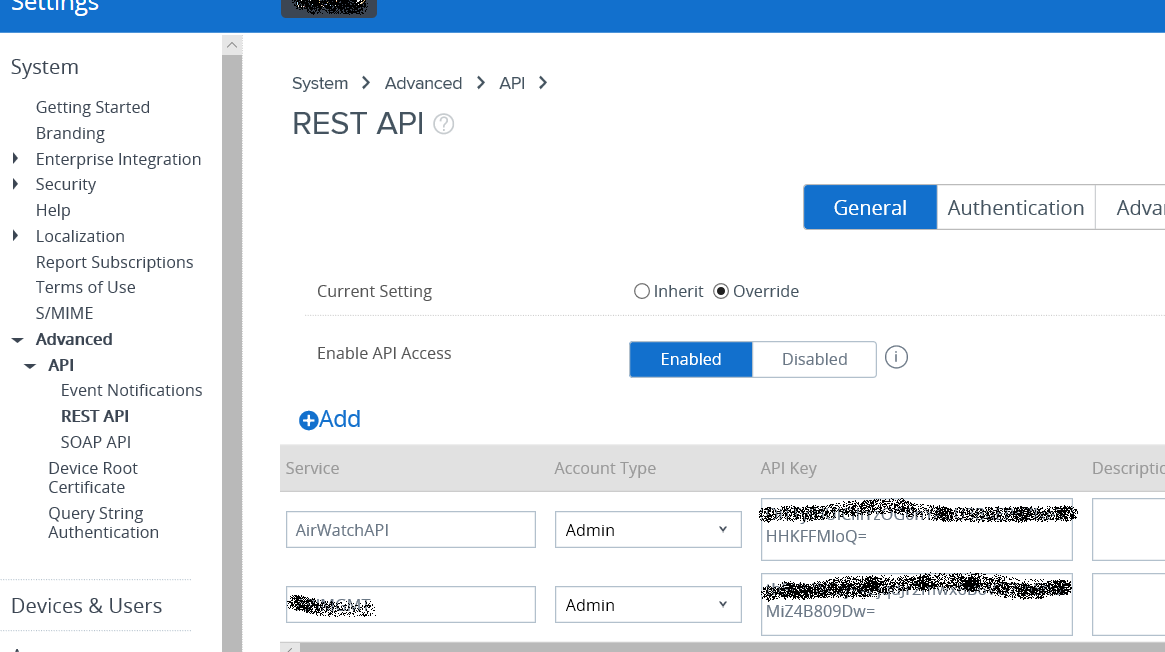
Copy and paste that somewhere where you can use it later. You could add a new service to get a new key if you like. This is also known as your aw-tenant-code.
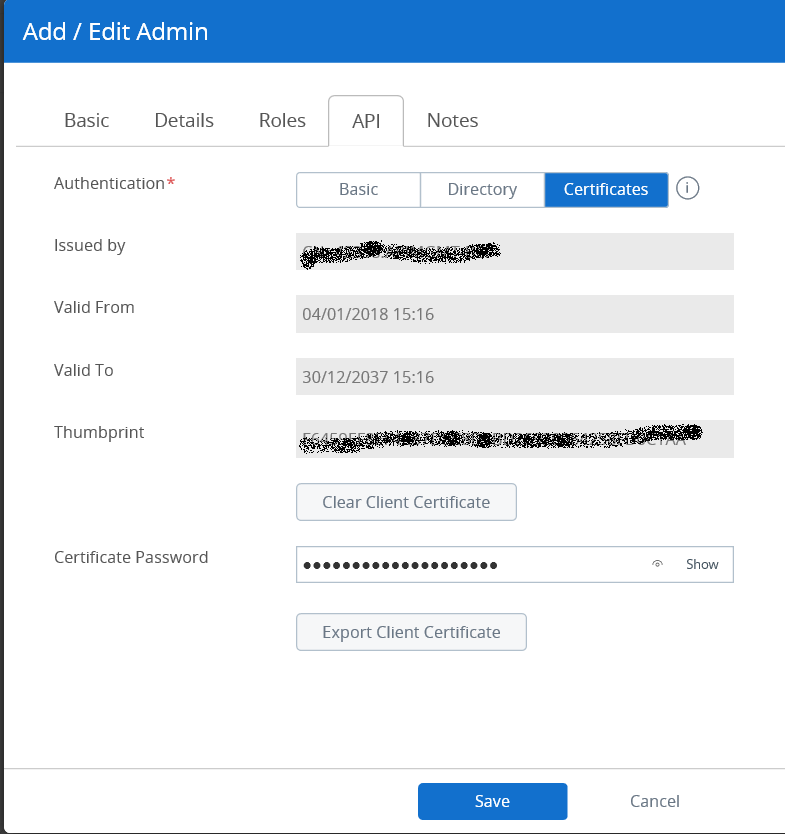
You then need to create a user account to connect. Ideally you should be using a different account from your normal console based admin account, so you can then set a role later. For now, we will create a new account and use a console administrator role though. To do this, go to Accounts>Administrators>List View, and press Add. Choose "Add Admin". Enter a username, such as APIMGMT, enter a password, username, and email address. Go to the Roles tab, and set it as a console administrator (unless you have another role already defined). Then go to the API tab, and choose "certificate". Enter a certificate password and then press "save". Then enter the certificate password and export the certificate.
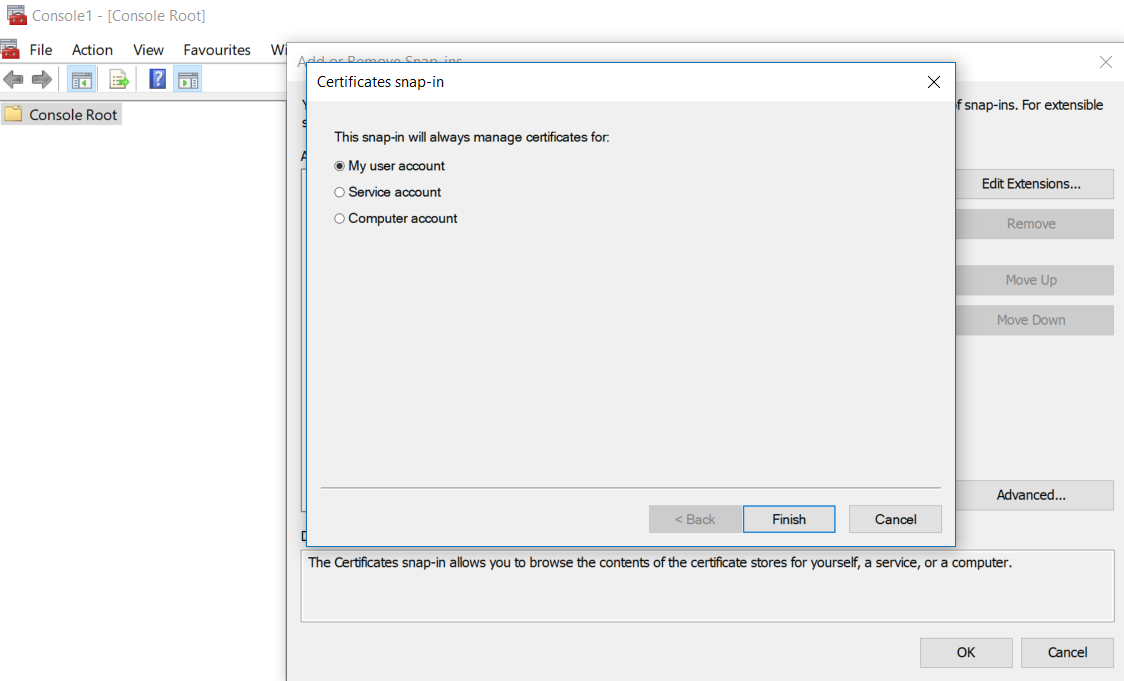
You then need to import this certificate. Open MMC, and import the Certificates snap-in. Be sure to select the option to manage certificates for "My user account".
Go to Certificates - Current User>Personal>Certificates, and import the certificate from Airwatch. You will need to change the default file type in the browse box to the second option, as th is a .p12 file. Once imported, copy and paste the name somewhere, as we will need that later too.
So, so far, you should have retrieved your:
- aw-tenant-code
- Certificate, imported into your Current User certificate store.
The next post will show how to connect with Powershell.
comments powered by Disqus